How To Read Email Headers
·
Oct 23, 2017
Key Takeaways
Email headers reveal the true origin and path of a message, essential for deliverability and security troubleshooting.
Headers contain authentication signals like SPF and DKIM, which confirm whether a message was legitimately sent.
Accessing full headers varies by email client, but Gmail provides an easy “Show Original” view.
Understanding “From,” “Mail From,” and DKIM domains helps identify who actually sent the message.
SPF, DKIM, and (eventually) DMARC validation results confirm if a message passed authentication checks.
Q&A Highlights
Why are email headers important?
They contain rich metadata showing where a message came from, which servers handled it, whether it passed authentication, and whether anything suspicious occurred during transit.
Who benefits from learning how to read headers?
Developers, marketers, security teams, abuse engineers, and anyone responsible for deliverability, debugging, or validating message authenticity.
How do you view email headers in Gmail?
Open the email → click the down-arrow beside “Reply” → choose “Show original”. This exposes the raw headers and message payload.
What does the “From” header represent?
The brand or sender name that appears to the recipient in their inbox — the human-friendly identity.
What is the “Mail From” / Return-Path field used for?
It identifies the domain responsible for SPF verification and controls bounce handling. It often differs from the visible “From” address.
What is the DKIM domain?
It’s the domain that cryptographically signs the message. DKIM ensures the message wasn’t altered in transit and confirms the sender’s legitimacy.
How do you check SPF and DKIM results?
Look for authentication results in the headers:
spf=pass indicates the sending IP was authorized.
dkim=pass indicates the message was successfully signed and validated.
What about DMARC?
DMARC alignment is also reflected in header results, though deeper discussion is typically covered separately. It ties SPF and DKIM together under a single policy for stronger authentication control.

So you want to decode email headers
So you’re looking to boost your email game, get your hands dirty and stay in the running to be the world’s best email sender — or something like that. This post will give you a practical understanding of email headers, their importance, how to access them and how to read them.
Why should you read on?
Email headers provide rich information to help with any number of investigations. Most importantly, email headers provide a means of verifying the origin of a message. Other cool beans things headers help with are;
Authentication results (SPF/DKIM). These are critical to solid deliverability!
Any hops the message may have taken along the way
Timestamps from when the message reached certain waypoints
Anyone working in the following areas should know the basics about email headers:
Developers
Marketers
Security/Abuse teams
Fellow dorm-room nerds (I thought you looked familiar!)
Step 1: Get to the Choppa! (e.g. head on over to your personal inbox)
Depending on which email client you use, mail headers can be presented with some variation, I’m a numbers guy, you’re a numbers guy…so, we’ll just pick Gmail. Find a message that was ‘promotional’ or ‘notification’ in nature, as this will yield the best demonstration use case. I’ve chosen the fine folks over at Pinterest. If your company already sends mail, those would be fine samples to use as well.
Step 2: Open the email in the reading pane
Adjacent the ‘Reply to button’ hit the down arrow (1), then ‘show original’ (2)
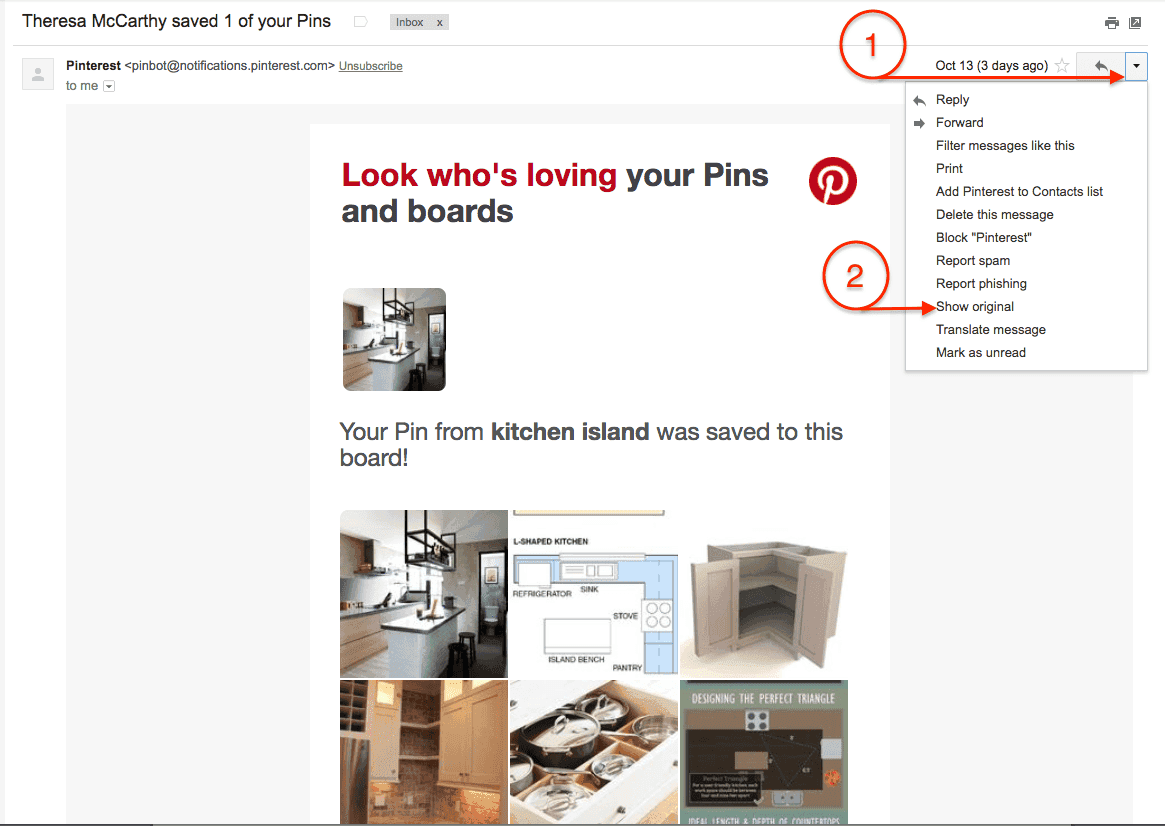
Eh voila, headers!. What you’re actually looking at here is a combination of headers and the message itself, in all of its parts (html, plain text version, to, from, subject, yada yada). For the purpose of this how-to, we’re going to avoid getting overtly technical and focus solely on the header portion. At the bottom of this post, I’ve included links some awesome extra credit reading.
Step 3: Who dis? (e.g. Finding the sender)
Let’s look for ‘who’ sent the message. This isn’t as easy to answer, as you’d think. Reason being is that some of the coolest companies on the planet actually make a living at helping other companies send their email (see what I did there? snort snort). In the spirit of keeping things basic, we’re going to show you a single-party example. You should know however that it’s not uncommon that a single message references multiple responsible parties. In the case of my example, it was transmitted using SparkPost.
Here are the three header values that carry the ‘who’ part.
Header field | What it tells you | Why it matters |
|---|---|---|
From | The sender name shown to the recipient | Can be spoofed, so not authoritative on its own |
Mail From (Return-Path) | Domain used for SPF validation | Confirms which domain is allowed to send the message |
DKIM domain | Domain that cryptographically signed the message | Verifies the message was not altered in transit |
‘From’: This is the entity that the recipient see’s in their email client.
‘Mail From’: This is the entity that is used for Sender Policy Framework (SPF). The SPF entity uses special DNS entries to ensure that the IP address used to transmit the message is authenticated. This header field has a few other names; Return-Path, envelope-sender and bounce domain.
DKIM domain: This is the entity that has signed the message. Signing a message is an important practice to ensure that the message was not altered in transit. DKIM also uses special DNS entries to ensure authenticity.
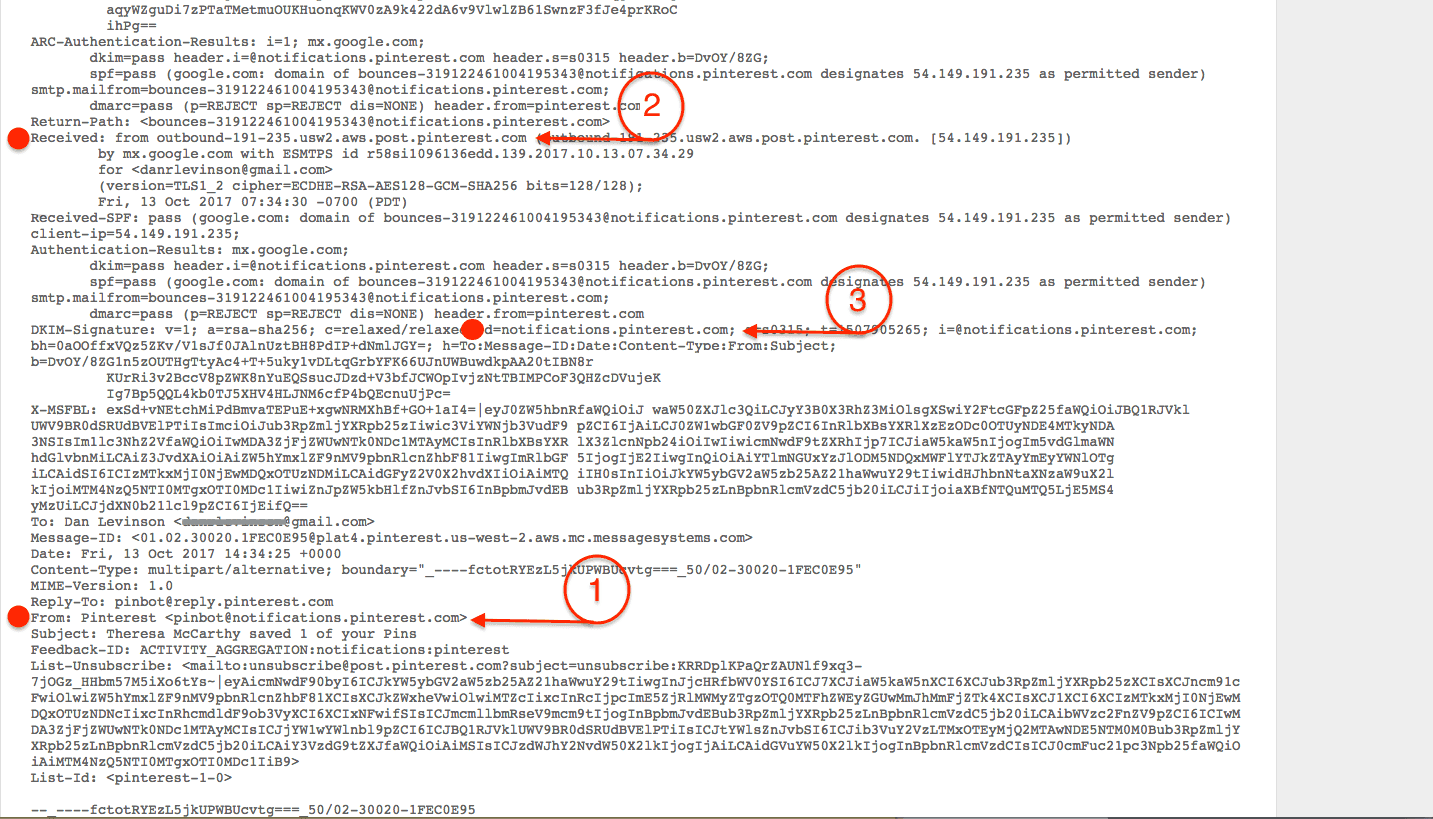
Step 4: I think he’s Five-oh (e.g. Checking Authentication results)
Now we know who sent it, let’s make sure this message was really sent by Pinterest.
SPF: You want to see a string match for ‘spf=pass’
DKIM: You want to see a string match for ‘dkim=pass’
DMARC: (separate blog post coming on this one. Be sure to bookmark our blog and check back in)
Congrats! You now know about 1000% times more about email then your downstairs neighbor.



